Cryptocurrency and crime go hand-in-hand, and that’s largely due to the anonymity of online transactions. Removing that anonymity is the golden ticket for law enforcement and intelligence agencies.
Using a few simple online investigation tools, and some good old tracing methods, we were able to trace the funding of a Syrian Jihadi cell, South African kidnappers, and an online scammer, all to one bitcoin address.
These finds were made by fusing OSINT (open-source intelligence) methods with cryptocurrency and blockchain knowledge. We hope that by sharing this case study with you, you can have the confidence to make your way through blockchain transactions and appreciate the larger picture of open-source evidence.
Using the blockchain in open-source financial investigations
Before we get stuck into how I traced these addresses, let’s take a look at the most important tool when it comes to cryptocurrency investigations: the blockchain.
These sequences, which are 26–35 characters long, are known as bitcoin addresses. They are unique to the owner that uses it and are part of a user’s bitcoin wallet. These keys, along with the time, and amount, is publicly available on the blockchain ledger.
This address is also what I give you when I want you to send me money, and as you will learn in this investigative piece, is very easily traceable.
Removing the anonymity of bitcoin addresses
A good analogy for a bitcoin address is a bit like a fingerprint on cash that is stored forever at the time of purchase. Of course, you can’t see that I just bought milk down the street, but you can certainly tell when I bought it, what address received the money and how much I have left in my account.
The anonymity comes into play when you try to figure out what I bought, who the person was that I sent the money to, and where it took place.
If an exchange can confirm an address, and has the identification to reveal an owner, then anonymity, for the large part, is removed.
The identification process of many exchanges involves a simple photo identification (usually government issued) and phone verification (via SMS). To combat the criminal use of cryptocurrencies, more and more exchanges are enforcing this identification standard.
Tracing the Syrian Jihadi Group
Having worked with the blockchain and cryptocurrencies in my own capacity, I felt quite confident when I saw a Jihadi cell put out a call for 100% anonymous donations to their bitcoin account, that I could find something interesting.
In a bid to raise money for “assisting front line Mujahideen” in Syria, an English-based campaign by Al-Sadaqah has been actively promoting photos of their fighters displaying banners with a bitcoin address.
They have promoted these largely through their Twitter and Telegram accounts. Below is an image I found on their Twitter feed.

The group claim in their Telegram channel that “Whoever is unable to take part in jihad physically but is abe to take part in jihad by means of his wealth, is obliged to take part in jihad by means of his wealth. So those who are well off must spend for the sake of Allaah”.

Tracing finances through the blockchain
There are two tools I use to explore the blockchain. The first is Blockchain.com which is a viewer for the blockchain ledger. The second is BitcoinWhosWho.com, which provides further details on bitcoin addresses and wallets as well as being a public database for reports of scams that have been linked to those addresses.
Using Blockchain.com, I was able to see the amount of money the Al-Sadaqah group has managed to raise since their first transaction in November, 2017.
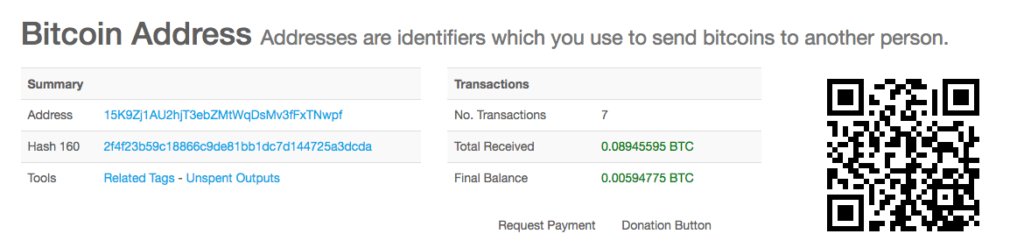
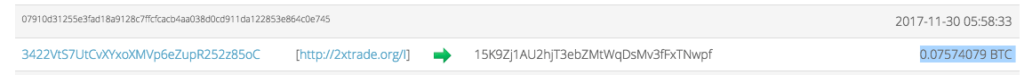
The account ending in 5oC is at the heart of this investigation, you are going to see it a lot. It is not an exchange wallet yet it sees a lot of money going in the wrong directions. One of the largest sources of funding to this address is a bitcoin exchange. At the time of writing this article, the 5oC account has more than 640 bitcoins (more than USD$4mill).
Running the 5oC address through BitcoinWhosWho reveals that the wallet has been labelled with a “scam alert” and has been reported for its link to a number of fake Bitcoin ponzi schemes, and other fraudulent activity.
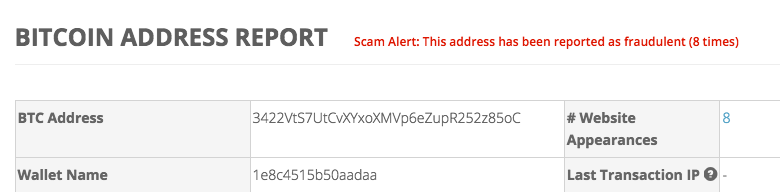
An interesting note that appears on BitcoinWhosWho is that the wallet has been linked to a child kidnapping case in South Africa, where ransom payment was demanded via Bitcoin.
I followed that case to see where it might take us. It led me straight back to 5oC.
Tracing the South African Kidnapping ransom payment
On 20 May, 2018, a young boy was kidnapped in South Africa by three men. A ransom note was left with the demand that 15 bitcoins be paid into a specific address.
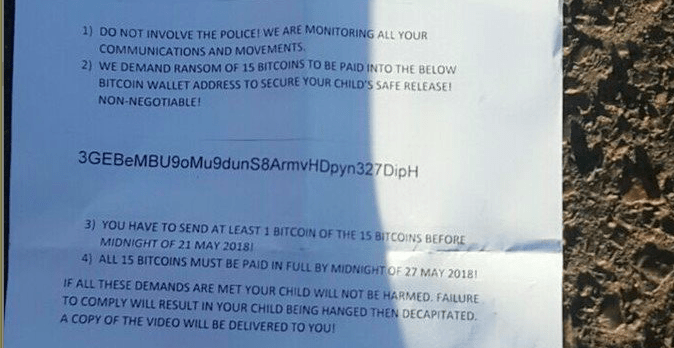
It was not known whether or not the parents made the full ransom payment, but the blockchain does show that 1 bitcoin was paid into the address on the note, as per the request of the kidnappers.
A number of significant payments that have also been made into the kidnapper’s address came from the same account that was funding the Jihadi cell in Syria: the 5oC account.
Finding the owner of 5oC — is it the scammer?
On BitcoinWhosWho, one of the scam warnings for our reoccurring 5oC address lists a cryptocurrency trading scheme known as EscOptions and its lead trader who goes by the name of “James Moore”.
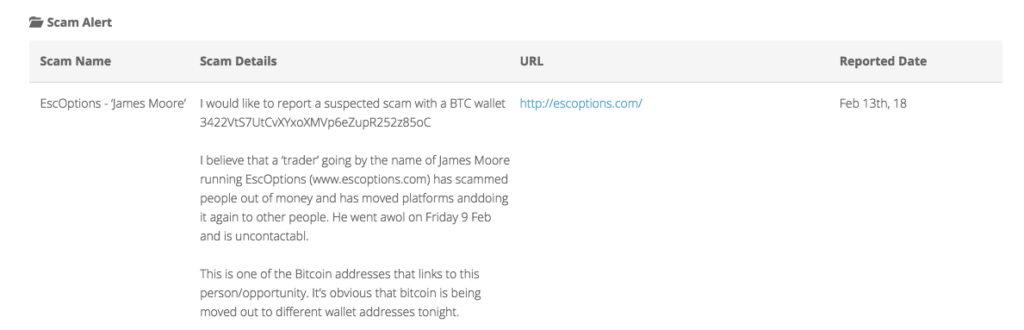
The page escoptions.com has been deleted, however another site listed as having an association to the 5oC address is traderushinvestment.com . At the time of writing this article, it is still up and running.
No information could be found about the owners of these sites through a WHOIS domain lookup as they are both using identity protection. Running a search through Facebook for “James Moore” and “Escoptions” lead me to finding two fake Facebook accounts set up as a way to funnel users into the “investment sites”.
There are a number of giveaways as to the fabrication of these profiles to make them look like real success stories on Facebook. In regards to the “James Moore” profile, James “lives” in the UK, and is “from” there, but photos of his bitcoin cashouts are in South African Rand (ZAR).
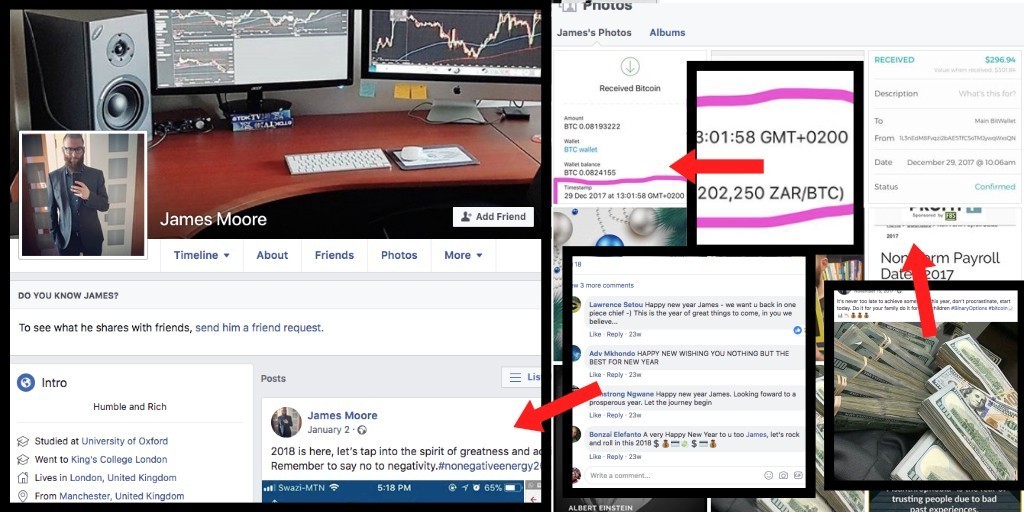
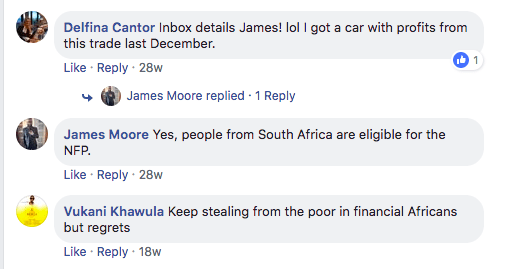
Using stalkscan engine, we can see that almost all of the pictures the fake account has liked are from South African accounts. Any comments given, or received are made from South African Facebook accounts and there is even a person (from South Africa) that has complained that “James Moore” is a scammer. A large number of the comments this fake account has received have come from similar accounts that are also actively promoting escoptions.com and other scam-listed sites.
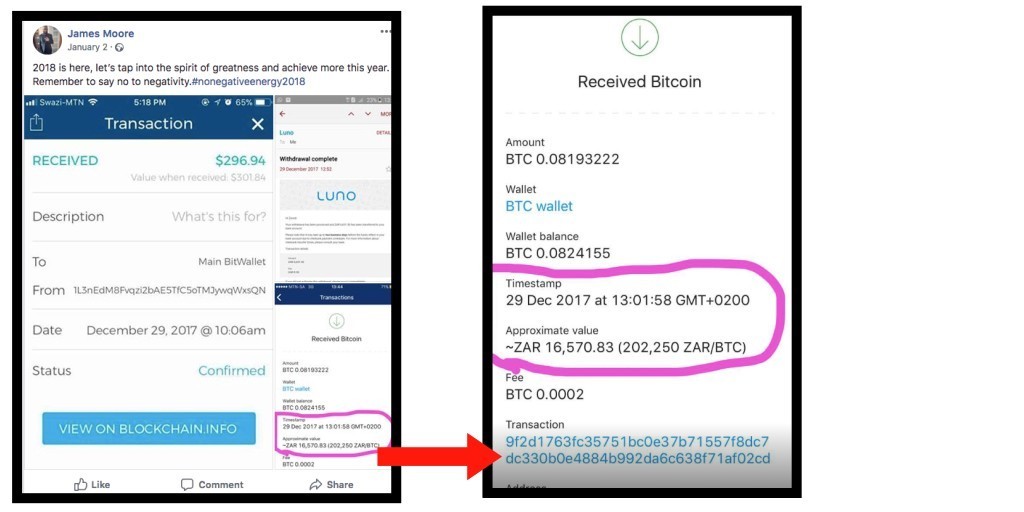
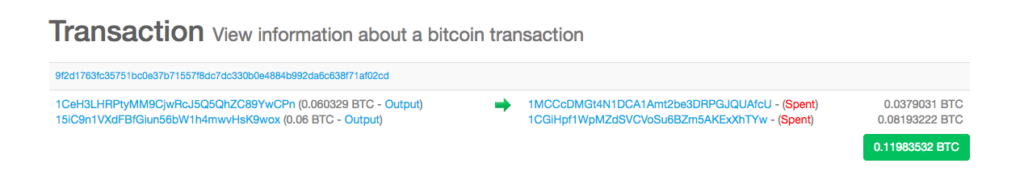
There are some key players that are traced from these addresses. The majority of the money in this transaction can be traced through from the TYw address and further into a much more valuable address ending in CbwP, which has exchange days exceeding amounts of more than USD$250,000 of trades.
CbwP’s purpose is to accumulate bitcoins from a large number of addresses, and send it all into two accounts. The first is the 5oC account, which has played a key role in the facilitation of many crimes. And the second is an address ending in 6BEp . The 6BEp bitcoin address has been listed as the recipient address for a number of scams in Southeast Asia. Any funds it receives are filtered back through to 5oC.
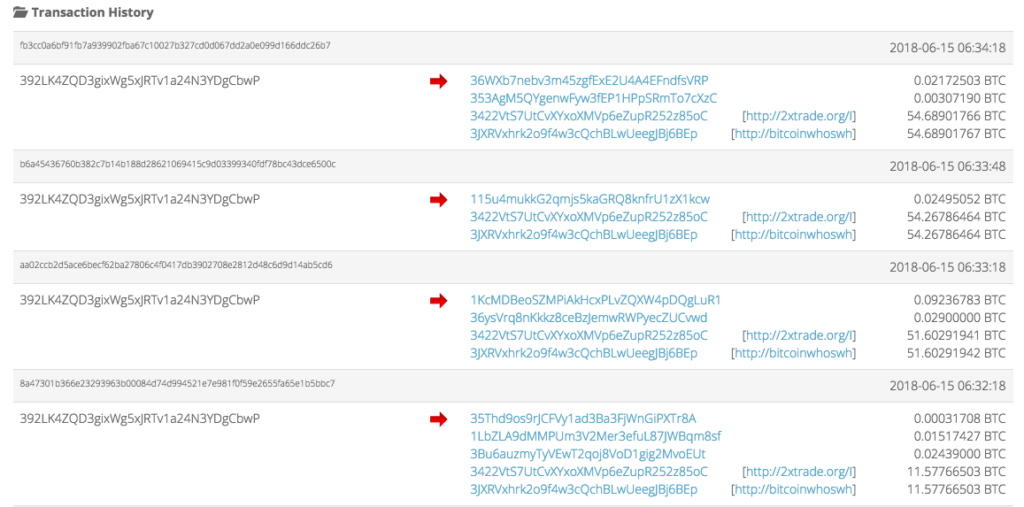
For the CbwP account, it contributes the largest amount of bitcoins into the 5oC account. In fact, if we take a look at the blockchain just for 15, June, 2018, we can see that several hundred bitcoins were sent to the 5oC address on that one day. That’s more than $4mill in one day.
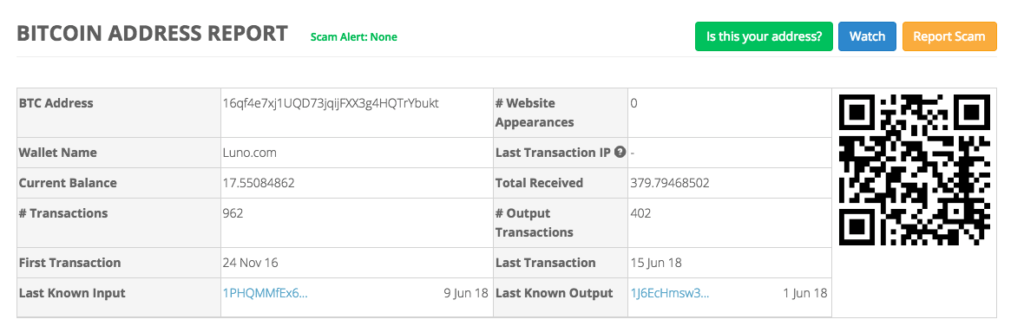
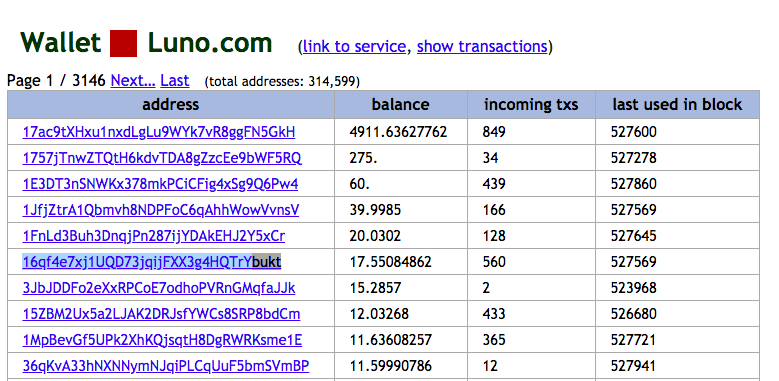
While it is generally quite difficult to confirm the details of who owns a address, Luno.com’s ownership of the bukt address can be verified by viewing BitcoinWhosWho, and WalletExplorer.com, which provides details on bitcoin wallets.
This identifies that our bukt address is a Luno.com exchange address.
The cryptocurrency exchange
Luno.com is a bitcoin exchange. It is a registered financial institution where you can buy bitcoins online.
There is a clear trail on the blockchain that shows significant funds moving from Luno.com’s exchange addresses through to the 5oC address (as seen below) which is responsible for funding the Jihadi movement in Syria, kidnappers in South Africa, and has links to a cryptocurrency scam network on Facebook.
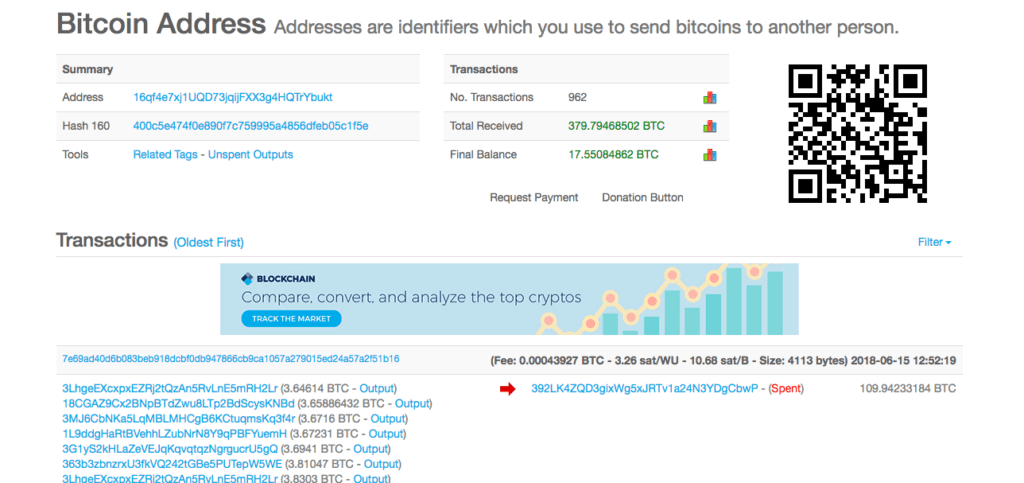
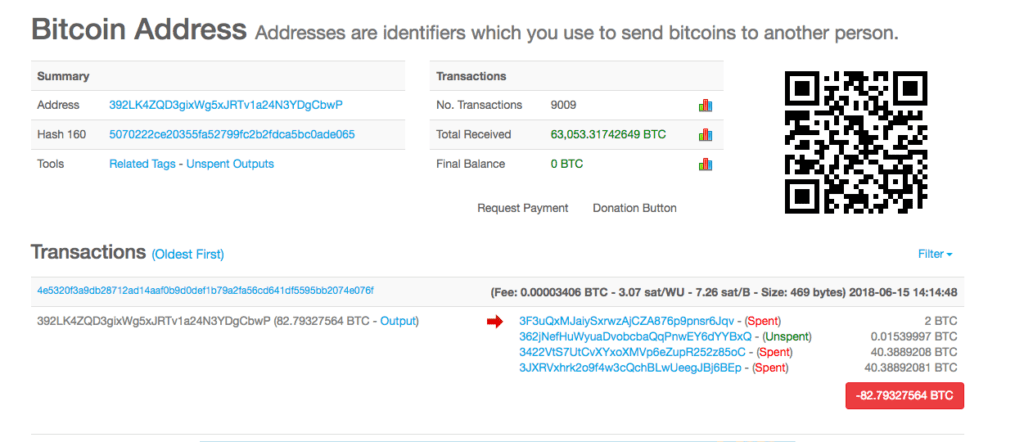
Luno.com has a strong presence in South Africa, where it was known as BitX up until 2015. It was founded in South Africa and moved into the European market after its rebranding.
Is 5oC scrambling the blockchain?
The 5oC address has remained a puzzle for me in a number of blockchain investigations I have conducted.
At all times, there has been an address, linked with criminal activity, that has sent proceeds to the 5oC address, and has resulted in a mass address flow to an exchange.
For open source investigations such as this, there is a need to provide evidence for every facet of the investigation. While there is no clear evidence stating this, I believe the 5oC address is a bitcoin tumbler, that scrambles a bitcoin transaction to make in untraceable on the blockchain.
Indicating factors that lead me to believe this are:
- The volume of traffic going through the 5oC address before being cashed in exchanges
- The volume of addresses involved in every hashed transaction (making it near impossible to trace a single payment)
- The volume of addresses involved in illegal activity that trace through to the 5oC address.
Unveiling cryptocurrency anonymity
What about that anonymity that I mentioned at the beginning of this post? How can it be revealed? Cryptocurrency exchanges like Luno.com have identification procedures for account holders to combat criminals hiding behind the shadows of bitcoin.
To make an account with Luno.com is quite simple, but to conduct any trading of more than 1000 Euro in deposits, or withdrawals, requires the identification standard of a mobile number confirmation, and basic personal details such as an address, age and email address.
This is described on Luno.com’s website as their “Know Your Customer” standard, and their compliance with Anti-Money Laundering standards to “prevent abuse” of their service.
The relationship between the individual addresses I have identified that are linked to crime and Luno.com is a serious concern.
A large amount of ‘untraceable’ funds moves from a registered exchange wallet, and into a bitcoin address that is directly linked with providing financing to Jihadi fighters and kidnappers, as well as being a centralised address for a considerable fraud network acting through social media.
A final note
There were no special secrets used in this tracing case study on active cryptocurrency crime, nor was there inside information. It is all accessible from your office, or couch at home.
Tracing through the blockchain is a simple activity, and the various tools I have highlighted in this case study have very easy-to-use interfaces. However, it is one of the many ways publicly available data can be scrutinized, and linked, to find the missing pieces.





